Ec2 Backup - An Overview
Wiki Article
The Definitive Guide for Rto
Table of ContentsThe Facts About Ec2 Backup UncoveredThe Buzz on Ransomware ProtectionThe 5-Second Trick For Ransomware ProtectionExcitement About Aws S3 Backup
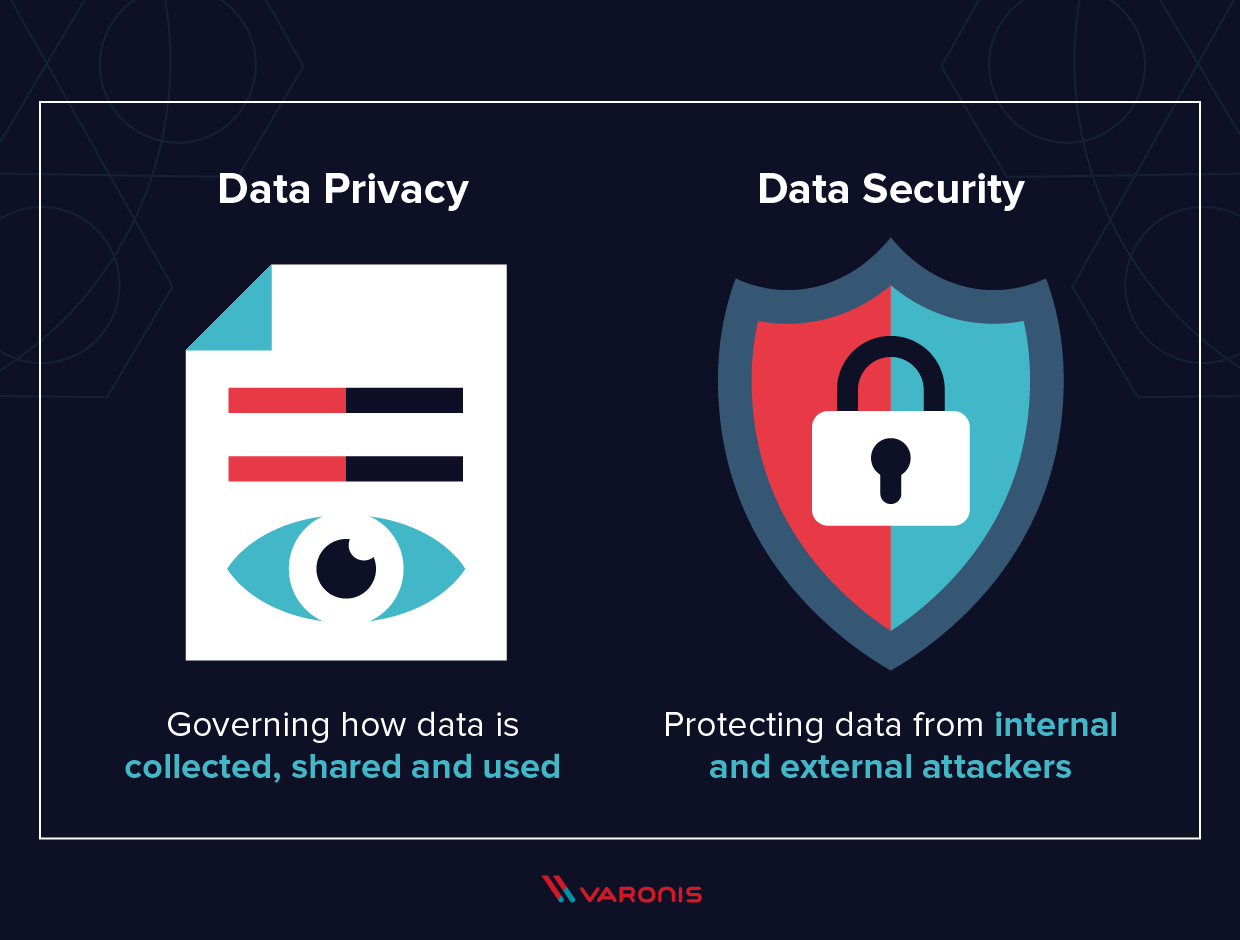
utilities that enable you to keep an eye on and filter network traffic. You can make use of firewall programs to ensure that just licensed individuals are permitted to gain access to or transfer data. controls that aid you verify credentials and also ensure that user benefits are applied correctly. These measures are normally used as component of an identity as well as access monitoring (IAM) remedy and also in combination with role-based gain access to controls (RBAC).Encryption shields your information from unapproved access even if information is taken by making it unreadable. Endpoint defense software generally allows you to monitor your network perimeter and to filter website traffic as required.
This can be done after data is refined as well as analyzed or periodically when data is no more appropriate. Removing unnecessary data is a need of numerous conformity regulations, such as GDPR. For additional information concerning GDPR, take a look at our overview: GDPR Data Defense. a set of practices as well as technologies that establish just how an organization handles a disaster, such as a cyber attack, all-natural calamity, or large-scale devices failing.
A Biased View of Rto
Lessening your information collection can also assist you save on data transfer as well as storage space. These systems use third-party information to confirm individuals as well as eliminate the need to shop or transfer user data to your systems - https://calendly.com/clumi0/30min?month=2022-11.
Reflecting this, GDPR has made user approval a vital element of data usage and also collection. You can be sure to include users and also their authorization in your procedures by designing personal privacy worries right into your interfaces. aws backup. As an example, having clear user notices describing when data is accumulated and also why. You must likewise include options for individuals to modify or opt-out of information collection.
Extremely often, information transportability indicates the ability to relocate data between on-premises data centers and the public cloud, and also in between different cloud companies. Information transportability additionally has lawful implicationswhen information is saved in various nations, it is subject to various laws and also laws.
How Data Protection can Save You Time, Stress, and Money.

This makes it challenging to relocate data from one cloud to another, and also produces vendor lock in. Progressively, companies are seeking standard ways of saving and taking care of information, to make it mobile across clouds. Mobile tool security refers to procedures created to protect sensitive information saved on laptop computers, mobile phones, tablet computers, wearables as well as various other portable tools.
In the modern IT atmosphere, this is an essential facet of network security. There are numerous mobile information safety devices, created to protect mobile tools as well as data by determining risks, developing back-ups, as well as stopping threats on the endpoint from getting to the business network. IT team use mobile information security software application to allow secure mobile accessibility to networks as well as systems.
Ransomware is a sort of malware that encrypts user information and demands a ransom in order to release it. Brand-new types of ransomware send the information to enemies before securing it, enabling the attackers to extort the organization, intimidating to make its delicate info public. Backups are an efficient protection versus ransomwareif a company has a current copy of its information, it can restore it as well as restore accessibility to the data.
Indicators on Aws Cloud Backup You Need To Know
At this phase ransomware can infect any type of linked system, including backups. data protection. When ransomware spreads to backups, it is "video game over" for information protection techniques, since it ends up being impossible Recommended Site to restore the encrypted data. There are several strategies for preventing ransomware and in certain, stopping it from infecting back-ups: The simplest technique is to make use of the old 3-2-1 backup rule, keeping three duplicates of the data on two storage media, among which is off facilities.Storage suppliers are using unalterable storage space, which guarantees that data can not be modified after it is stored (https://events.education.ne.gov/user/clumi0/). Huge organizations have actually numerous datasets stored in different areas, and also numerous of them might replicate information in between them.
It is no usage securing a dataset and also guaranteeing it is certified, when the data is duplicated in an additional unknown place. CDM is a kind of option that spots duplicate information as well as aids handle it, contrasting comparable data as well as enabling managers to erase extra duplicates. Catastrophe recovery as a service (DRaa, S) is a taken care of service that offers an organization a cloud-based remote calamity healing website.
With DRaa, S, any type of size company can duplicate its local systems to the cloud, as well as quickly restore procedures in instance of a disaster. DRaa, S solutions leverage public cloud framework, making it feasible to keep several duplicates of framework as well as information across numerous geographical locations, to increase resiliency. Data security requires powerful storage space innovation (https://www.directoryposts.com/author/clumi0/).
Report this wiki page